By Chris Topham, Abtec Building Technologies.
By Chris Topham, Abtec Building Technologies.
In Part 1 of this two-part series, we looked at simple ways to protect KNX projects from malicious attack over IP networks. In Part 2, we will explore some valuable tactics to protect your building management system (BMS). Whether you design, deploy or use KNX devices, this article will be a useful guide to protect your automation projects.
Eager to Connect
The chances of providing a KNX network in isolation are rare. We usually provide a head end or BMS to enable the user to control their building’s environment. KNX is a distributed intelligence system and its security is paramount to the safe operation of the building.
Many modern BMS, for example Tridium Niagara, Siemens Desigo or Loxone Miniserver, arrive with web services built in. These provide a variety of functions, including the ability to interrogate and adjust the BMS remotely over the Internet. Such web services are often pre-configured to make them easier to use, so it is important that we put in place security measures that are appropriate for the project.
BMS manufacturers take security very seriously, and many will provide setup wizards to assist in setting up these services. It is recommended however, that we add additional security; otherwise we could leave our projects vulnerable.
Where is the threat coming from?
Before we explore how to protect our projects, it is worth looking at the origins of the threats. The majority of issues arise when systems are connected to the web in order to aid remote monitoring. Without appropriate security, they can become beacons to the millions of automated web bots that exploit vulnerabilities.

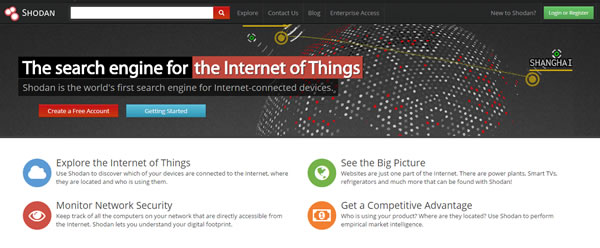
Shodan promotes itself as the world’s first search engine for Internet-connected devices, and provides users with the ability to find hardware that is connected to the web. Using this with the right search phrases, it is easy to build a list of unsecured BMS remote connections.
Securing your project
Each BMS is different; however here are some tactics that you should be able to use on most BMS.
1) Replace the default user name and password
If your BMS has a default username and password, replace the password, at least, with a strong password. A strong password has at least six characters, and uses a combination of upper and lower case letters, numbers and symbols. This will be the biggest deterrent to most malicious hackers. Get the system to prompt users to change their password at specified times, for example every three months.
2) Initiate web interface security
If your BMS has a webserver or web interface, there is a good chance that you will be able to implement security for this area. This usually means that when you attempt to visit the server remotely, you will be prompted for your user name and password. You would be surprised at just how many people do not initiate this.
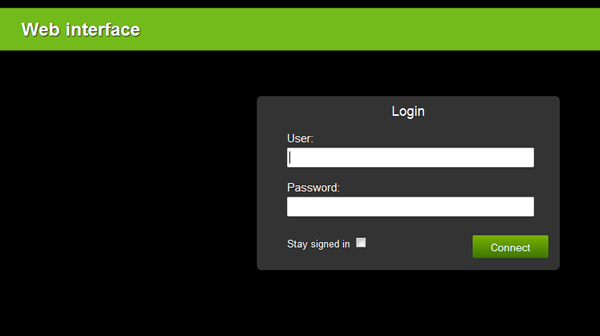
3) Restrict login attempts
Once the web interface security is set up, restrict the number of times users can attempt to log into it. Setting the number of attempts to three before the user is locked out, will help defend against ‘dictionary’ attacks whereby automated bots will enter every word from a dictionary one by one to find the password.
4) Create user roles and profiles
Many BMS support profile-based roles. This means that different users will have access to different areas of the system. This can help prevent users accidentally deleting important files. Always create an individual user account for each person that needs access to the system. Do not use shared login details.
5) Turn off redundant services
If you are not using other web services, such as SSH or FTP, close these through the configuration of the BMS, if possible. If your BMS doesn’t give you that option, use a firewall to block ports.
6) Add a firewall
Rather than connecting the BMS directly to the Internet, add a hardware firewall. A popular tactic is to restrict all traffic to the BMS and then to add a remote connectivity rule. This could be a VPN (Virtual Private Network), preferably using the SSL (Secure Socket Layer) protocol created for web browsers. You could even extend this to restrict access to all IP addresses other than your own.
7) Don’t use the Internet
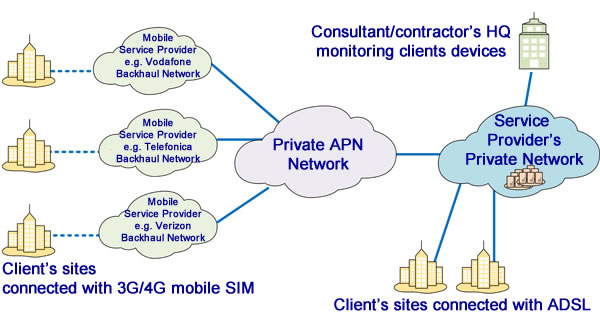
If your KNX project contains sensitive elements, for example building access control, it would be worth avoiding the Internet altogether. Using a private network, preferably one specifically designed for building controls, you can avoid most of the issues mentioned above. A private network uses the same connection technology as normal Internet access, such as DSL and 3G/4G among others. The difference is that the traffic on a private network doesn’t travel over the Internet, and is therefore much more secure. Remote access can be achieved by connecting to that private network provider’s remote gateway via sophisticated, robust security technology.
Use the experts
Taking these steps can help secure your KNX project. The amount of effort put into securing the project will be defined by the needs of the project and the client’s budget. For larger, complex projects, it would be worth contacting a networking security specialist, preferable one that understands building control protocols. They will be able to test the security of your project to ensure that your organisation’s brand doesn’t become a headline for all of the wrong reasons!
Chris Topham is Head of Marketing for Abtec Group. The Abtec Group includes Abtec Building Technologies Ltd, a building automation organisation and Abtec Network Systems Ltd, an IT networking specialist for the construction industry.
For a concise guide to providing secure remote access to building management systems, Abtec has prepared a white paper titled Providing Remote Access Connections for Building Services Projects.