By Mark Warburton, Ivory Egg.
By Mark Warburton, Ivory Egg.
Over the last month during a few talks and presentations I’ve given, it has become clear that the security of KNX and other IoT systems is still a concern for a lot of people. It’s great that people are aware of the potential risk when connecting a building to the Internet, since one of the biggest risks is carelessness.
There are countless ways of making a KNX installation both accessible from the outside and also secure and protected from those with malintent. However, let’s start with the method that is unsecure and definitely not recommended.
Unsecure KNX systems
Assuming you are using the standard ports or multicast address on a IP interface or router, it’s possible to open the same ports in the firewall, thus making the KNX system immediately accessible from outside. However, as these are standard, and are left the same on most installations, it doesn’t take much effort to identify them and potentially gain access to an installation. In fact, at the 2016 KNX Technical Conference, Friedrich Praus from FH Technikum Wien, presented that between 8th August and 25th October 2016, 6163 KNX systems were identifiable online, completely accessible and unsecured.
Obviously, this approach is bad practice, especially given they have been deliberately put online in all likelihood to provide remote access for the integrator or the user.
So, onto the more secure methods of remote accessing a KNX installation.

More secure KNX systems
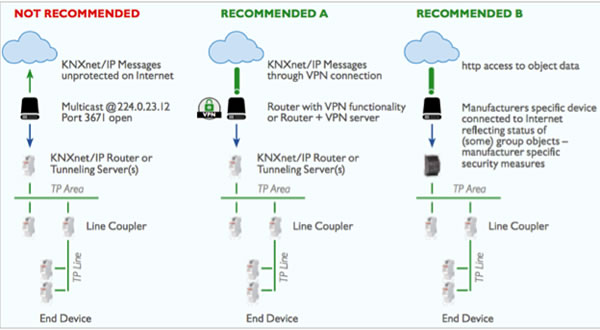
The first is to create a VPN (Virtual Private Network) in order to create a secure tunnel into the system. Once the authentication has been used to connect you, you are effectively local within the building, allowing you to make any changes needed or connect apps or visualisation.
One way of creating a VPN is to use a network router that has an embedded VPN server. We find that on most installations where systems are being installed in the home, such as AV, CCTV and KNX, then it’s more likely the network will be fully managed by the integrator. On smaller installations or where the homeowner isn’t willing to put in a more advanced router than the standard unit supplied by the Internet service provider, then another solution is needed.
In this case, it’s possible to install a separate VPN server within the property. A great example of this is the Gira X1, which has an OpenVPN server that is embedded. The installation is quite simple, with the only major complication being the need to open some ports on the router. However, unlike opening ports directly to a KNX interface or router, the X1 requires credentials to prevent unauthorised access. Via the X1 and the OpenVPN server, it’s possible to not only allow access for remote control for the X1 app, but you can also access devices on the rest of the network such as the KNX system or a CCTV camera.

Another step forward in ease of setup is the Smart Connect KNX Remote Access from Ise. This works in a similar way to a VPN but instead of a tunnel, it uses a secure website to encode all traffic in and out of the installation. Because the Ise device makes the first connection out of the building, a secure path is created, meaning there is no configuration required on the network router. By either running an application on a remote computer or logging in via the secure website, it is possible to access the network devices within the home. Some visualisation systems such as the Gira Homeserver also support the Ise remote access device, meaning remote connections are completed without first needing to connect a VPN.

The three solutions above are all summarised in this graphic from the KNX Association, and are covered in the KNX secure position paper.
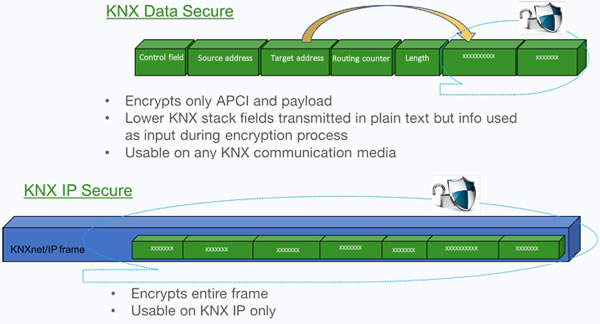
KNX Data Secure
The first is KNX Data Secure which allows device objects to have a layer of security. Using industry-standard security algorithms, the application data within a KNX telegram is encoded using keys shared between devices. This is supported as of ETS 5.5, so we are now waiting for manufacturers to catch up. This will be a great tool for securing and encoding key information on the KNX bus, or eventually, making the entire bus unreadable unless you have the project with the keys.
KNX IP Secure
The other method is KNX IP Secure. This approach takes the existing KNX IP telegram and wraps it in a security blanket, again using an industry-standard approach. The primary application of this is to encode the communication between two or more IP routers that are being used to create an IP backbone. It can also be used to encode the traffic from ETS to an IP router or interface, and in time we will see all IP communications being secure. Again, it is up to KNX manufacturers to develop and release KNX products as the KNX Association has already done the work to make this possible. There will also be a requirement for third-party systems that currently connect via an IP router or interface to support KNX IP Secure, but only time will tell how quickly this is adopted.
Conclusion
The likelihood of a system being hacked by someone with malintent, as opposed to someone seemingly hacking for the sake of it, is extremely low. However, the arguments above once again show that the KNX Association is ahead of the curve in ensuring that KNX remains relevant in this age of increasing security concerns and threats.
As long as integrators continue to perform their role correctly and ensure that they install systems in a safe and robust way, then we, as an industry, have nothing to worry about.
Mark Warburton is the Technical Director of Ivory Egg (UK) Ltd, a supplier of leading KNX products and provider of KNX training courses.