Whether a client’s home control system has access to the Internet for remote control, monitoring or maintenance reasons, Simon Buddle explains how to use a VPN to protect the connection.
I have just returned from a fantastic week away skiing. It has been a holiday in the making for more than two years; repeatedly cancelled due to Covid-19. We thought, once again, we had been foiled by the closing of the French borders to the British, but we found a port that was still open, and we jumped through it. The Swiss let us in.

Much has been said in relation to smart home systems and cyber-attacks. When you think of the world of computers these days, they are all interconnected in some shape or form. We are connected via routers to the Internet, our office PCs are all connected on the local area network and countries are connected via huge fibre optic bundles that often lie on the seabed. It is a completely connected world, truly global, machine-to-machine, connected through thousands of miles of cables.
Whether it’s a border or a router, people will always try to exploit a weakness, and given the right knowledge – which lots of people have – it is easy to hack into a machine or system on the other side of the world.

Opening TCP port 3671 has historically been used to provide remote access into a KNX system. It also opens a connection into the customer’s local area network and can be used for malicious purposes. It is, in effect, a window into a house, that has been left wide open, and if you know where to look and how to access it, you can walk in without any requirement for security checks.
Having said that, we now have an armoury of great KNX devices that can provide secure tunnels to the system. The Jung KNX IP Router and the Gira S1 are two obvious examples. These establish a link out of the property without creating unsecure access routes into the customer’s home PC network. But you could choose from any number of manufacturers including Basalte, Weinzierl, Siemens, Schneider and ABB – all offer products to solve that puzzle.

The Virtual Private Network
It is quite likely that the KNX system or bus is not the only device that we may need to remotely connect to, and that does pose a subtly different challenge. How do I connect to the Siemens PLC that runs the plant room? Or the Intesis AC, Modbus or BACnet interfaces?
The most obvious and secure solution here is to use a VPN (Virtual Private Network). But how do we set this up, and is it secure? Let us answer the second part first. It is very secure (assuming your passwords etc are too). It creates a secure virtual point-to-point tunnel over the Internet between your computer and the client’s LAN. Once connected, your computer appears on the client’s network.
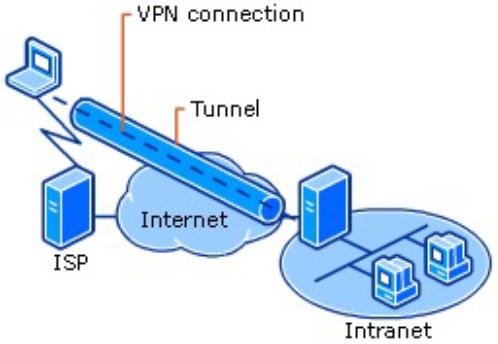
To create a VPN without the use of software such as OpenVPN or NordVPN, there are two basic requirements:
1) a fixed Internet IP address or a router that supports DNS.
2) a router that supports VPN connections.
1) The fixed IP address or router that supports DNS
Imagine being a postal worker delivering mail, day in, day out. Except that every day the house numbers change, so number 32 is now twenty houses away. This is analogous to your Internet IP address. Every time your router restarts it will receive a new IP address from your Internet Service Provider (ISP). This means that we no longer know where you live, so to speak. So, the fixed IP address solves that problem. The other way is to provide a DNS (Dynamic Name System). DNS essentially provides a lookup service for Internet addresses. Each time your router’s Internet IP address changes, the router sends out the new address to the DNS server so that your record can be updated. You can then use the DNS name (which does not change), for example myhouse@dyndns.org.
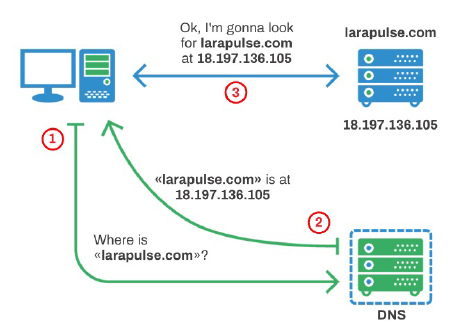
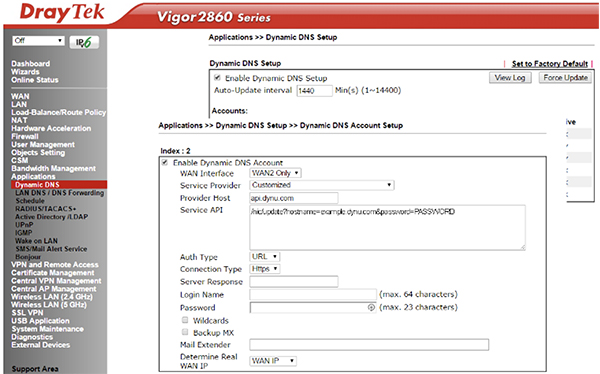
That is the first part of the VPN configuration dealt with. You can now always find the customer’s router on the Internet using a DNS service.
2) The router that supports VPN connections
There are two steps to creating a VPN. Firstly, you have to create a ‘user’. The username and password will be required when you connect over VPN. The second element is to setup the VPN connection protocol. Common protocols are PPTP, IPSec, L2TP and SSL Tunnel. PPTP has weak security and is no longer supported by Apple devices. The most commonly used is L2TP with a ‘preshared’ key. Most DrayTek routers support DNS and VPN setup and enable easy access to the client’s LAN.
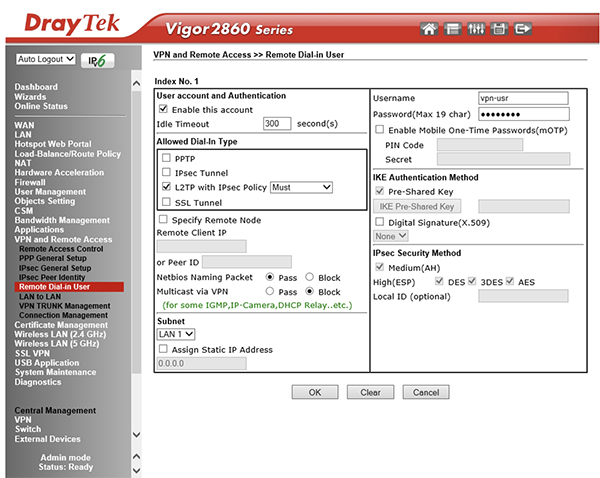
Now it is just a question of setting up the VPN profile on your laptop or desktop PC using the same login criteria. Help is at hand here as DrayTek also offers a small VPN client software package that makes it simple. Of course, Cisco, Unifi and hundreds of other router manufacturers offer the same functionality. The ones that do not are BT, Sky and Virgin, i.e. all the ones given away by ISPs. So, if you want to access the client’s network over VPN, you will certainly need to supply a router to do the job.
Conclusion
Imagine when you get that phone call from a client that says, ‘Such and such has stopped working’ and being able to reply, ‘I’ll login right now and check what’s going on’. That’s got to be a worthwhile service that is truly invaluable to your customers. With the right router and one hour of your time, it is easy to learn how to setup a VPN connection. That hour will save countless hours of travelling backwards and forwards to site.
However, if there’s a way in to your client’s system from the outside world, it is imperative to make sure it cannot be exploited by those with malicious intent.
For me, setting up a VPN is one of the most valuable skills I have learnt. You can sit at your desk and view all data in real time as it happens, have multiple PCs connected to the same house watching every system signal, without getting out of your pyjamas. And better still, you can roll that skill into a remote monitoring and maintenance offer, thereby earning some money from it.
Simon Buddle CEng MIET, is a consultant for Future Ready Homes, a specialist in BMS and ELV services system design.