Steven De Bruyne discusses why every KNX installation should be evaluated for security, and what measures KNX Association has taken to ensure they can remain safe.
There are many ways in which a building automation system can be attacked. The most typical is being hacked via unprotected Internet access, but there are other ways too, including physically cutting into cables, sniffing messages, or interfering with devices in unlocked cabinets. Then there are the people who can access the installation, such as family members, colleagues in an office, hotel guests, customers in a shopping mall or the entire world via unprotected Internet access.
KNX installations are no exception in terms of likely attack, but what sets them apart are the measures that KNX Association has taken to ensure that they can be kept safe.

What should be protected?
Security should always be considered in any new installation and be re-considered for existing ones. The KNX Security Checklist can be a great help in this, as well as the How to Prevent Access to KNX Installations online course that KNX Association has put together. A more comprehensive KNX Secure Guide, intended for both installers as well as KNX manufacturers, is also available.
Security should firstly protect communications. In terms of data security, installations should be protected against unauthorised data manipulation, blocking and theft. The idea is to prevent an unauthorised party from understanding the messages, and from manipulating or injecting their own messages. Secondly, the KNX devices should be protected, so that they cannot be reprogrammed or even made inoperable.
Ultimately, especially in terms physical attacks, it is down to the KNX professional and their customer to identify the risks and consequences, and agree on the most appropriate course of action. As far as data attacks are concerned, there are some basic security steps that should be considered from the outset, and KNX Secure devices, developed by KNX manufacturers according KNX Association’s standard, should be an important part of the solution.

Security should be considered from the early design of an installation, and this includes evaluating the risks and consequences. If no KNX Secure devices can be chosen, then other measures to protect the installation should be taken. KNX IP interfaces can, for instance, be avoided, couplers can be parameterised for best security, and the cabling and mounting of devices can be re-considered.
Whilst many existing installations will have been functioning reliably for years, they may have been designed in times when security was not such an issue, and will therefore be open to possible attack through, for example, unprotected Internet accessibility. As a matter of urgency, these should be checked and protected by using state-of-the-art equipment.
What are the different types of KNX security available?
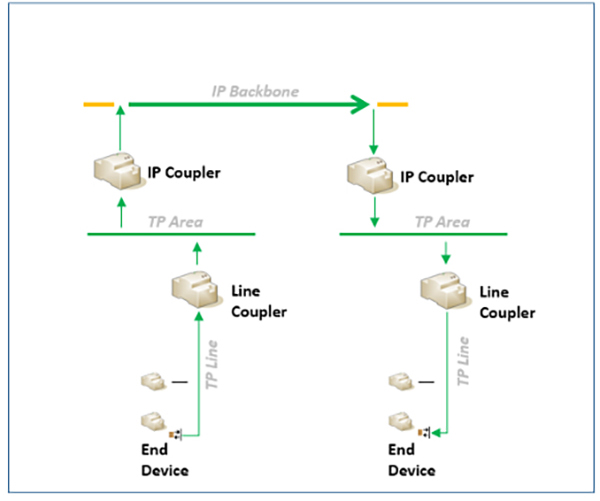
KNX Secure offers two types of security, namely KNX IP Secure and KNX Data Security. KNX IP Secure protects the KNX IP protocols (device management, tunnelling and routing) by encrypting the communication and only allowing authenticated communication partners.
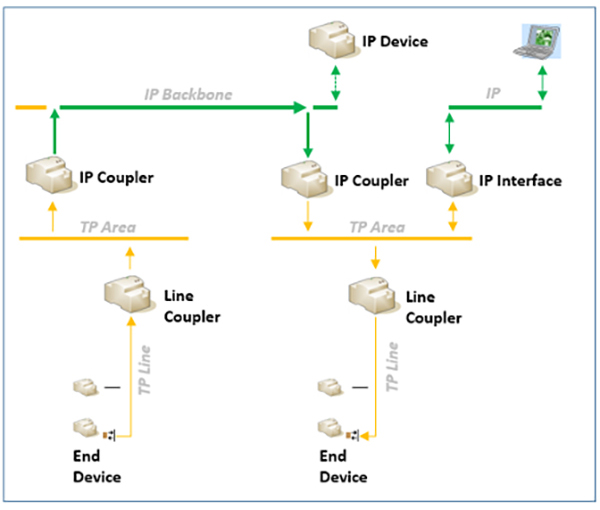
KNX Data Security on the other hand, runs on the KNX twisted pair (TP1) cable and KNX RF. It mainly encrypts and authenticates the message payload and prevents devices from being modified without proper key.
Conclusion
Attempted hacking of KNX installations is no longer an academic hypothesis – it happens in real life, so you must make sure that your projects are protected. KNX Security gives you peace of mind about the robustness of your installation against hackers whilst protecting your work and investment. KNX manufacturers are already offering this additional functionality, the technology will continue to evolve and the KNX Security protocols will be kept state-of-the-art.
For the latest tips on how to protect your system, use the KNX Security Checklist, the KNX Secure Guide and the 30-minute online course on How to Prevent Access to KNX Installations.
Steven De Bruyne is a System Architect for KNX Association.