Michael Critchfield explains why remote access is desirable, what the pitfalls can be, and how to ensure it is secure.
KNX Secure, including both IP Secure and Data Secure, readied the KNX Standard for greater expectations and regulations on cyber security. KNX Secure supports the most secure encryption standards according to ISO 18033-3, such as AES 128 CCM encryption, to effectively prevent attacks on the digital infrastructure of buildings. Through IP Secure, it keeps the IP communication safe between KNX Secure devices by extending the IP protocol in such a way that all the exchanged data is completely encrypted. At the same time, through Data Secure, it protects user data against unauthorised access and manipulation by means of encryption and authentication.
KNX installations could be protected against attacks, and nowadays, the choice in KNX Secure-capable devices has grown significantly. However, in existing KNX installations, potentially without KNX Secure, but with the convenience of remote access enabled, there is often another pressing concern.

Remote access
Remote access to your KNX installation is a wonderful concept, and not a new idea. Long before installations could take advantage KNX IP Secure, the demand was there to enable access to a KNX installation from anywhere in the world – a great idea, when done right.
There are various reasons why remote access is desirable. First, a change of season is normally a key time for performing maintenance visits, as some parts of the system may have been redundant for the last few months. Whilst there are always elements of a system that require on-site inspection, finding ways to test and support systems remotely means more convenience for both parties and reduced site-visit costs. Second, remote monitoring by the systems integrator can help detect any problems and even anticipate them before they become an issue. And third, users can make the home comfortable in time for their imminent return.
Don’t leave the front door open
Historically, in some cases, remote access was implemented by ‘opening the front door’ so to speak, i.e. using unauthorised port forwarding through port 3671 on the network router – the simplest approach and at little-to-no extra upfront cost.
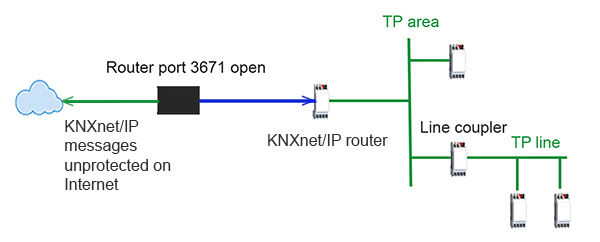
Owners of a network were unlikely to know that their network router was set up with port 3671 open, and whilst this would allow the owner to have remote access, unless some additional measures were taken, it would also allow anybody else to enter, simply by knowing the KNX installation’s IP address. So, if the network were paired with a KNX installation, unless KNX IP Secure and Data Secure were in place, those with bad intentions would be able to gain access through the router and potentially control and track bus communication.
Times have changed. We have KNX Secure, and we know better than to just forward the KNX port 3671. Options include enabling KNX Secure, setting up dedicated networks, standard firewall protocols and authorised access to remote access gateways, using VPNs (Virtual Private Networks), or even setting a BCU (Bus Coupling Unit) password to your KNX installation as a last resort.
Granted, there is a slightly greater effort upfront, but you’ll thank yourself in the long run.
KNX Security Check
KNX Association is constantly on the move, extending the KNX Standard and bringing better, more secure solutions to the market. In 2024, we released the KNX Security Check.
With this tool you can check your own current IP address for an open port 3671. It only takes a few seconds – and you’ll know whether you are secure or need to act now.
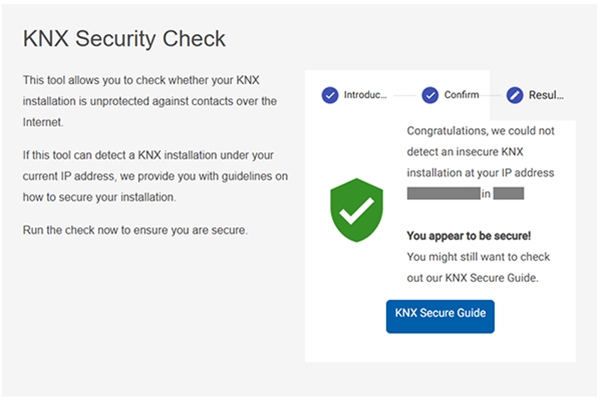
When triggered by the user, the security check tool sends a KNXnet/IP description request to port 3671 of the user’s current IP address. Ideally, and in most cases, the request is ignored by the user’s router (timeout), which means that a connection cannot be established, no KNX installation can be found, and the user appears to be secure. In the worst case, however, a router configured to keep port 3671 open will allow the KNXnet/IP description request through to the KNX installation, and its IP interface will respond with its MAC address and device name.
No harm is done by the tool, but the result will inform the user that action must be taken to secure the KNX installation.
Conclusion
Run the KNX Security Check to find out whether your network router has port 3671 open. If so, the Security Check tool, which is available in multiple languages, provides helpful information on what to do.
Michael Critchfield is the ETS Product Manager at the KNX Association.